I was invited in April 2018 to join a team at the Blockchaingers Hackathon in Groningen, the Netherlands. Billed as one of the largest (if not the largest) hackathons in the world. Teams were asked to run their code through Better Code Hub (BCH) to check it for code quality.
We were told by the organizers if a team could break or find an error with the BCH system, we would get additional points for the hackathon. Game on. I like a challenge.
In looking at how BCH operates, once you log in with your GitHub credentials, it allows you to see your repositories and have them analyzed. Not going to bore you with what it looks for as you can read their site.
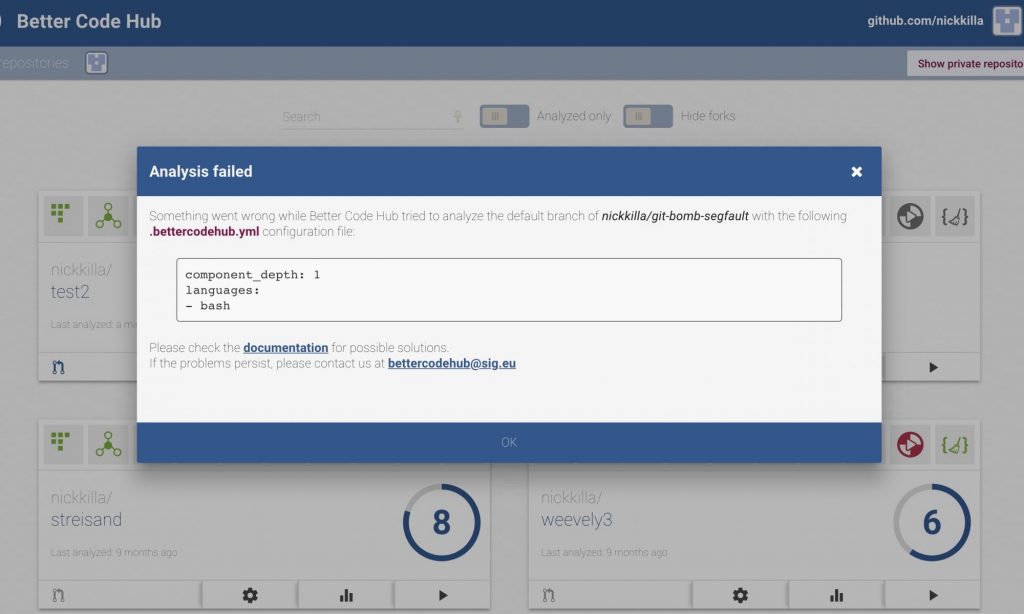
I logged in and used some of my pen testing scripts for tests to see what and how it would analyze. So their backend system clones my repo and then analyzes it via a new worker daemon. I wondered since it cloned the repo, how it would handle a classic Gitbomb. I cloned Kate Murphy’s repo for her bomb and ask it to analyze that repo. BCH threw an error stating it could recognize the type of code and thus couldn’t perform the analysis. Makes sense as there was no real code in that repo.
I then copied in a simple script written in bash and added a .yml file to override the defaults and state that inside the repo there is bash code. This time BCH tried to analyze the code. After about 15 mins, it errored and said just something went wrong. Bingo. Seems I broke something. So I tried to quickly run it again and upon clicking the analyze button again nothing would happen. I would need to wait about 2-3 minutes before I could try again.
We took my findings to the BCH reps on site (as they were a sponsor). They asked me to replicate what I had done and also let them manually clone the repo to check. They had the same error when they ran the analysis on the manually cloned repo. I was asked to check in later as they wanted to try and see what was happening on the backend and would need to call their tech team.
A few hours later I went back and I learned that after checking the logs, they noticed the backend checking system trying to analyze the Gitbomb and that caused it to take all the CPU/Ram for the system and it would crash the backend. The system would restart thus the delay in re-analyzing the repo I noticed.
They claimed they would look into ways to mitigate this and update the backend. As a thank you they provided me some limited edition GitHub stickers.
Upon checking today (I gave them enough time to fix the issue before making it public), the system still errors on the analysis but it doesn’t fully crash the backend.
EDIT: Saw this website discuss the Hackathon and the use of BCH by the teams, so wanted to link incase anyone wanted to see further. https://hackernoon.com/writing-quality-code-under-time-pressure-62ebeb5f39c5